A digital signature—a type of electronic signature—is a mathematical algorithm routinely used to validate the authenticity and integrity of a message (e.g., an email, a credit card transaction, or a digital document). Digital signatures create a virtual fingerprint that is unique to a person or entity and are used to identify users and protect information in digital messages or documents. In emails, the email content itself becomes part of the digital signature. Digital signatures are significantly more secure than other forms of electronic signatures.
What is a digital signature?
Digital signatures have various uses and applications, including financial transactions, software distribution, contract management, and other scenarios where it’s important to authenticate a document while deterring any forgery or tampering. In an age where data breaches are rampant, understanding what a digital signature is can be your first line of defence against cyber threats.
A digital signature is a mathematical protocol that uses cryptographic techniques to verify the authenticity and integrity of digital messages or documents. It functions as the digital equivalent of your physical autograph or stamped seal but extends beyond merely imitating your handwritten name on a document. Digital signatures provide far more inherent security to authenticate identities in digital transactions.
The key aspects that define digital signatures and their purpose include:
- Authenticity: A valid digital signature on a document or communication exchange provides the recipient with confidence that the source originated from a known sender.
- Integrity: Digital signatures indicate that the contents of a given message or document have original integrity and have not been altered in transit.
- Security: Digital signatures use cryptographic techniques to provide high levels of security and universal acceptance. They are based on the Public Key Infrastructure (PKI) standards, which involve using a digital certificate for identity verification.
- Legal Significance: In many countries, including the United States, digital signatures are used to create a legally binding arrangement or document in the same manner as traditional handwritten signatures.
Difference between a Digital Signature and Digital Signature Certificate
Digital Signature
The Digital Signature is a method of confirming the authenticity of a transaction, document, or message. It guarantees that the sender generates the message/document and is not modified by the external party.
Digital Signature Certificate
Digital Signature Certificate functions similarly to identification cards issued by recognized (government) authorities. The certificate provides the following security benefits:
- Details of Certifying Authority
- Name & other information of the subscriber
- Subscriber’s public key
- DSC validity period
How do digital signatures work?
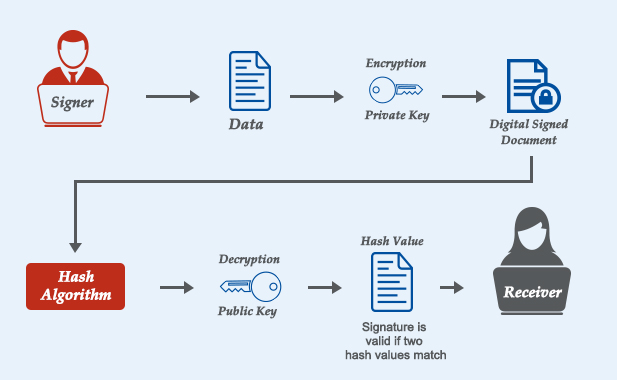
- Hash function — A hash function (also called a “hash”) is a fixed-length string of numbers and letters generated from a mathematical algorithm and an arbitrarily sized file such as an email, document, picture, or other type of data. This generated string is unique to the file being hashed and is a one-way function— a computed hash cannot be reversed to find other files that may generate the same hash value. Some of the more popular hashing algorithms in use today are Secure Hash Algorithm-1 (SHA-1), the Secure Hashing Algorithm-2 family (SHA-2 and SHA-256), and Message Digest 5 (MD5).
- Public key cryptography — Public key cryptography (also known as asymmetric encryption) is a cryptographic method that uses a key pair system. One key, called the public key, encrypts the data. The other key, called the private key, decrypts the data. Public key cryptography can be used several ways to ensure confidentiality, integrity, and authenticity. Public key cryptography can
- Ensure integrity by creating a digital signature of the message using the sender’s private key. This is done by hashing the message and encrypting the hash value with their private key. By doing this, any changes to the message will result in a different hash value.
- Ensure confidentiality by encrypting the entire message with the recipient’s public key. This means that only the recipient, who is in possession of the corresponding private key, can read the message.
- Verify the user’s identity using the public key and checking it against a certificate authority.
- Public key infrastructure (PKI) — PKI consists of the policies, standards, people, and systems that support the distribution of public keys and the identity validation of individuals or entities with digital certificates and a certificate authority.
- Certificate authority (CA) — A CA is a trusted third party that validates a person’s identity and either generates a public/private key pair on their behalf or associates an existing public key provided by the person to that person. Once a CA validates someone’s identity, they issue a digital certificate that is digitally signed by the CA. The digital certificate can then be used to verify a person associated with a public key when requested.
- Digital certificates — Digital certificates are analogous to driver licenses in that their purpose is to identify the holder of a certificate. Digital certificates contain the public key of the individual or organization and are digitally signed by a CA. Other information about the organization, individual, and CA can be included in the certificate as well.
- Pretty Good Privacy (PGP)/OpenPGP — PGP/OpenPGP is an alternative to PKI. With PGP/OpenPGP, users “trust” other users by signing certificates of people with verifiable identities. The more interconnected these signatures are, the higher the likelihood of verifying a particular user on the internet. This concept is called the “Web of Trust.”
Digital signatures work by proving that a digital message or document was not modified—intentionally or unintentionally—from the time it was signed. Digital signatures do this by generating a unique hash of the message or document and encrypting it using the sender’s private key. The hash generated is unique to the message or document, and changing any part of it will completely change the hash.
Once completed, the message or digital document is digitally signed and sent to the recipient. The recipient then generates their own hash of the message or digital document and decrypts the sender’s hash (included in the original message) using the sender’s public key. The recipient compares the hash they generate against the sender’s decrypted hash; if they match, the message or digital document has not been modified and the sender is authenticated.
Type of Digital Signature Certificates
Sign DSC- This type of DSC can be used for signing documents. The most popular usage of this type of DSC is signing the PDF file for filing on Government websites. Signing via DSC gives the assurance of the integrity of the signer and the data. It is proof of unhampered and unaltered data.
Encrypt DSC- Encrypt DSC can only use to encrypt a document. It is mostly used in the tender portal to help the organization to encrypt documents. Encrypt DSC is useful for documents that are highly confidential and contains information that needs to be protected.
Sign & Encrypt DSC- Sign & Encrypt DSC can use for both signing and encrypting. A signature certificate is used to sign a document, while an encryption certificate is used to encrypt the data. It is suitable for users who need to authenticate and maintain the confidentiality of the information shared.
Classes of Digital Signature Certificates
Certifying authorities issue three different types of DSCs. Depending on their purpose and requirements, applicants can choose from three types of digital signature certificates.
Class 1 DSC- Class 1 Digital signatures are used to verify an email address’s association with a person. It is not used for validating any documents and therefore holds no legal validity in the signing of documents.
Class 2 DSC- Class 2 Digital signatures are used to verify a person’s identity against a pre-verified database. This type of Digital Signature is issued to a person as a USB token and is used for company registration, LLP registration, IT return filing, MCA returns filing, and IE code registration and for filing documents with the Ministry of Corporate Affairs and the Income Tax Department.
On 26-November-2020, The Controller of Certifying Authorities, India (CCA) issued guidelines to the Certifying Authorities (CA) stating that only class-3 Digital Signature Certificates (DSC) will be issued from 01-January-2021. Certifying Authorities (CA) is not issuing class 2 DSC (fresh and renewal) from 01-01-2021. However, the existing class-2 DSC will remain valid till its expiry.
Class 3 DSC
Class 3 Digital signatures are the most secure form of Digital Signature certificates used to establish the identity of the signee in e-commerce and e-tendering. For instance, many online e-tenders require auction participants to participate in the bidding using a Class 3 Digital Signature to establish their acceptance of the bid electronically. Class 3 DSC can also be used for trademark registration. Class 3 Digital Signatures are issued after the Registering Authority verifies the identity of the applicant in in-person.
Class 3 Digital Signature can be used for the following purposes:
- MCA e-filing
- Income Tax e-filing
- e-Tendering
- LLP registration
- GST application
- IE code registration
- Form 16
- Patent and trademark e-filing
- Customs e-filing
- e-Procurement
- e-Biding
- e-Auction and more
Components of a Digital Signature Certificate
- Public Key – This is required as part of a verification system.
- Name and Email Address – This is required for contact information purposes and ease of identification.
- Name of the Company – This section identifies the company that owns the Signature.
- Serial Number of the Digital ID – This part is a unique number bundled with the Signature for tracking ad extra identification reasons.
- Digital Signature of the Certification Authority – This is a signature of the DSC’s issuing authority.
Validity of Digital Signatures
DSCs are generally valid for one or two years; however, this certificate is renewable. Submit the request for renewal of DSC not less than 45 days before the expiry of the validity period for the DSC.
Prescribed Authority to Issue the DSC
To get the Digital Signature Certificate, the applicant needs to apply to the Certifying Authority for the issuance of DSC.
The Office of the Controller of Certification Agencies appoints the Certification Authorities under the Information Technology Act, 2000. Consequently, CCA has given authority to 8 Certification Agencies to issue DSCs to persons seeking the same.
The list of these Certification Authorities is as follows:
- National Informatics Centre (NIC)
- IDRBT Certifying Authority
- SafeScrypt CA Services
- SIFY Communications Ltd
- (n) Code Solutions CA
- E-MUDHRA
- CDAC
- NSDL
- Capricorn
- PantasignIDSIGN
- Versys
- XtraTrust
Benefits of a Digital Signature Certificate
- Authentication: A digital Signatures Certificate also helps create the document’s authenticity, which can use in court as a shred of evidence.
- High Security- A DSC reduces the chances of fraud and alteration of the document/message. This certificate makes sure that the Signature is verified.
- Cost-effective: A digital signature certificate reduces the cost required to complete a transaction because the DSC holder is not required to be present in person to carry out or authorize a business transaction.
- Time- Effective: As DSC is in the virtual format, the documents can sign with one click; it saves time and is quicker and cheaper.
- Easy Verification: The DSC holder can present the DSC to government agencies to facilitate quick verification of the business transaction if needed.
Importance of DSC for Compliances
- Individuals and entities must get their accounts audited and file their income tax returns compulsorily using a DSC.
- The Ministry of Corporate Affairs (MCA) has a mandate for companies to file all reports, applications, and forms using a DSC.
- A company can only get GST registration by verifying the application through a digital signature.
- DSC is necessary even for filing all Governmnet applications, amendments, and other related forms.
Format of Digital Signature
There are two formats of Digital Signature certificates.
- PFX File
- USB Token
PFX File
PFX File is a Digital Signature Certificate that is in a file format (.pfx format). This type of signature can be easily circulated through e-mail, which makes it easier for users. However, there is a risk of misuse if not handled properly.
USB Token
A Digital Signature certificate in a USB Token looks similar to a pen drive, which is attached to the PC for using a digital signature. The main advantage of it is that it safeguards DSC from misuse which is more likely in a pfx file.
FAQs
How Does a Digital Signature Work?
- Hashing: The document is passed through a hash function to produce a unique hash value.
- Signing: The hash value is encrypted with the sender’s private key, creating the digital signature.
- Verification: The recipient decrypts the digital signature using the sender’s public key to obtain the hash value. The recipient also hashes the original document and compares both hash values. If they match, the document is verified as authentic and unchanged.
What is a Digital Signature?
A digital signature is a cryptographic technique used to verify the authenticity and integrity of digital messages or documents. It ensures that the content has not been altered since it was signed and that the signature is genuine.
Practice area's of B K Goyal & Co LLP
Income Tax Return Filing | Income Tax Appeal | Income Tax Notice | GST Registration | GST Return Filing | FSSAI Registration | Company Registration | Company Audit | Company Annual Compliance | Income Tax Audit | Nidhi Company Registration| LLP Registration | Accounting in India | NGO Registration | NGO Audit | ESG | BRSR | Private Security Agency | Udyam Registration | Trademark Registration | Copyright Registration | Patent Registration | Import Export Code | Forensic Accounting and Fraud Detection | Section 8 Company | Foreign Company | 80G and 12A Certificate | FCRA Registration |DGGI Cases | Scrutiny Cases | Income Escapement Cases | Search & Seizure | CIT Appeal | ITAT Appeal | Auditors | Internal Audit | Financial Audit | Process Audit | IEC Code | CA Certification | Income Tax Penalty Notice u/s 271(1)(c) | Income Tax Notice u/s 142(1) | Income Tax Notice u/s 144 |Income Tax Notice u/s 148 | Income Tax Demand Notice | Psara License | FCRA Online
Company Registration Services in major cities of India
Company Registration in Jaipur | Company Registration in Delhi | Company Registration in Pune | Company Registration in Hyderabad | Company Registration in Bangalore | Company Registration in Chennai | Company Registration in Kolkata | Company Registration in Mumbai | Company Registration in India | Company Registration in Gurgaon | Company Registration in Noida | Company Registration in lucknow
Complete CA Services
RERA Services
Most read resources
tnreginet |rajssp | jharsewa | picme | pmkisan | webland | bonafide certificate | rent agreement format | tax audit applicability | 7/12 online maharasthra | kerala psc registration | antyodaya saral portal | appointment letter format | 115bac | section 41 of income tax act | GST Search Taxpayer | 194h | section 185 of companies act 2013 | caro 2020 | Challan 280 | itr intimation password | internal audit applicability | preliminiary expenses | mAadhar | e shram card | 194r | ec tamilnadu | 194a of income tax act | 80ddb | aaple sarkar portal | epf activation | scrap business | brsr | section 135 of companies act 2013 | depreciation on computer | section 186 of companies act 2013 | 80ttb | section 115bab | section 115ba | section 148 of income tax act | 80dd | 44ae of Income tax act | west bengal land registration | 194o of income tax act | 270a of income tax act | 80ccc | traces portal | 92e of income tax act | 142(1) of Income Tax Act | 80c of Income Tax Act | Directorate general of GST Intelligence | form 16 | section 164 of companies act | section 194a | section 138 of companies act 2013 | section 133 of companies act 2013 | rtps | patta chitta